Overview of Identity and Access Management (IAM)
The field of Identity and Access Management (IAM) is evolving rapidly, moving beyond simple usernames and passwords to a more dynamic, secure, and user-centric model. The core trends are driven by the rise of remote work, cloud adoption, sophisticated cyberattacks, and privacy regulations.
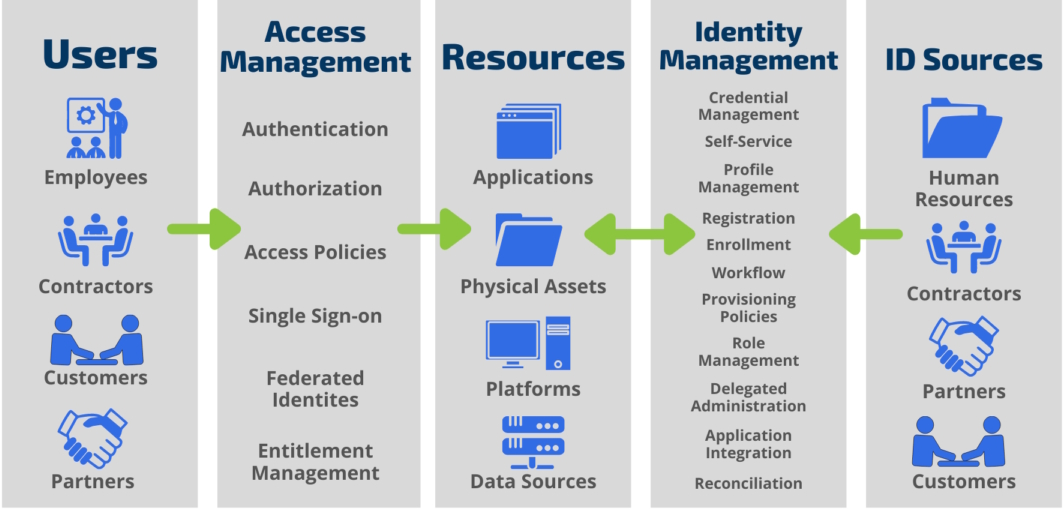
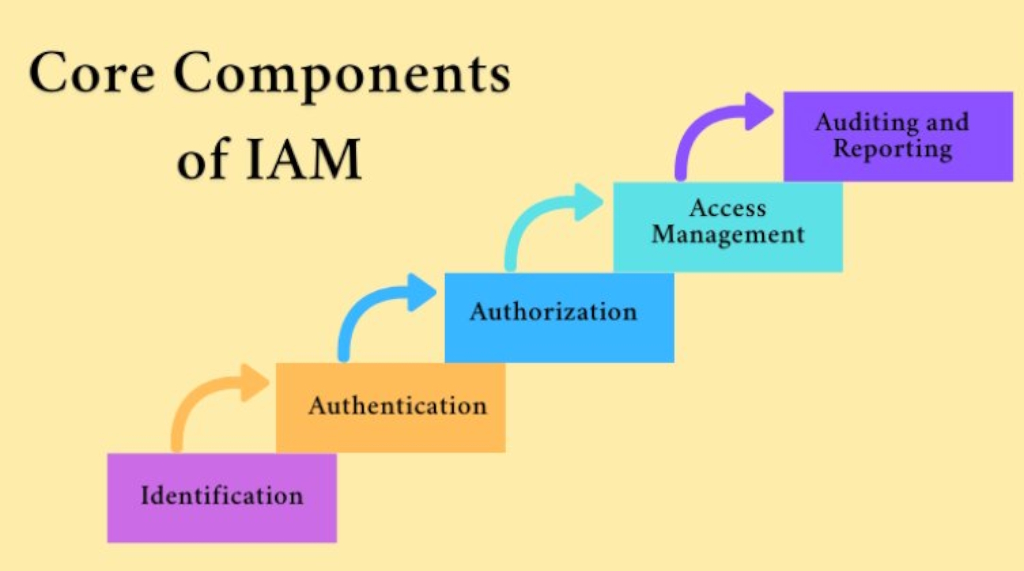
Identity and access management (IAM) refers to the processes, practices, and technologies related to managing identity information, including authentication, authorization, and accounting. IAM helps ensure the access rights of individuals are applied as needed based on their business roles or relationships in an organization. It is the combination of business processes, policies, and technology solutions that enable an enterprise to manage the roles and privileges for personal users and devices to be able to access business systems. Gartner provided a wacky definition of IAM: “The discipline that enables the right individuals to access the right resources at the right times for the right reasons.”

IAM solutions provide identity and authentication protection by offering role-based access to corporate systems. Roles can be defined based on an employee’s job title and authority or roles can be assigned to applications or devices that may also require access to corporate systems. Third parties such as contractors or customers can also be granted limited access. IAM systems mainly perform three basic tasks: identifying, authenticating, and authorizing. This means that only the intended persons are allowed access to specific hardware, software, applications, and IT resources—as well as specific data and content—to perform tasks. An IAM framework includes components such as:
- User: An identity that has associated credentials and permissions
- Group: A collection of users that specify permissions for multiple users to give administrators an economy of scale
- Policy: Permissions and controls to access a system, resource, data, or content, within a business context
- Role: A set of policies, typically corresponding to the minimum set of privileges needed to perform a particular business function, such as accounting or marketing, that can be applied to users or groups.
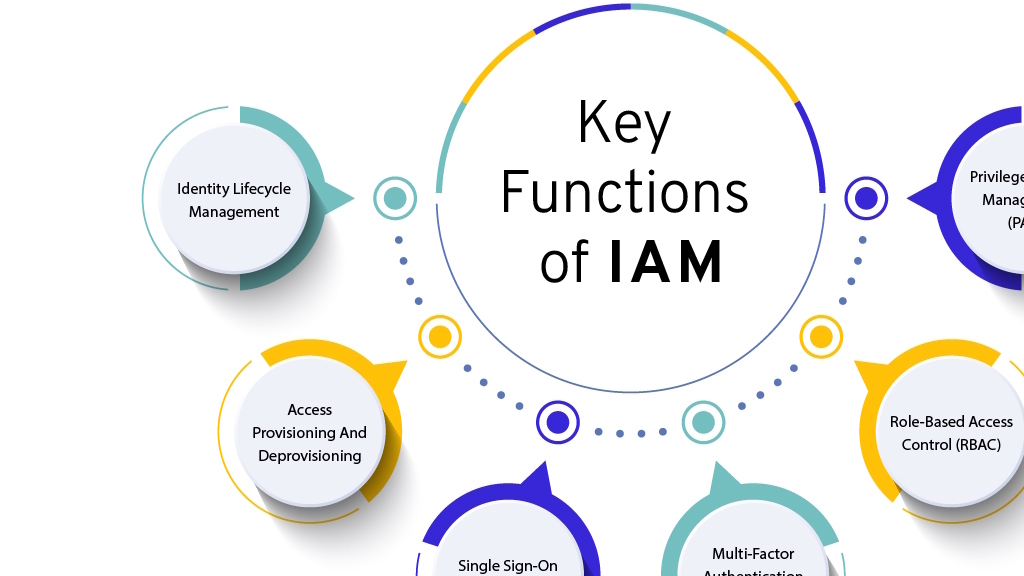
So we are going to try to identify new trends in Identity and Access Management (IAM) including the widespread adoption of AI and machine learning for automation and threat detection, the move toward passwordless and phishing-resistant authentication, and the rise of Zero Trust Architecture. Other key trends are the increasing adoption of decentralized identity, IAM's evolution to support multi-cloud environments, and the need to plan for post-quantum cryptography. .
The Paradigm Shift: Beyond Passwords & Perimeter
Long are gone days when users could have logged into their compputers by using just username and password. With the latest Windows 11 relaese 25H2, Microsoft wants user to use a Microsoft account for Windows and its products to, as official word is, to "integrate services, sync settings across devices, and ensure a more seamless experience with cloud-based features". In reality they are more concerned with increasing data collection, as linking accounts allows the company to gather more information.
In the last couple of years, the IAM has shifted beyond passords in the following way:
- Passwordless Authentication: This is arguably the biggest and most user-friendly trend. The goal is to eliminate the weaknesses of passwords (phishing, reuse, cracking).
- Technologies: FIDO2/WebAuthn standards are leading the charge, using biometrics (fingerprint, facial recognition) or physical security keys (YubiKey) for login. Other methods include magic links sent via email and one-time codes from authenticator apps.
- Zero Trust Architecture (ZTA): The old "trust but verify" model is dead. Zero Trust operates on "never trust, always verify."
- Identity is the New Perimeter: In a Zero Trust model, every access request is authenticated, authorized, and encrypted, regardless of where it comes from (inside or outside the corporate network). IAM is the central enforcer of this policy, continuously validating user and device identity.
Core Technology & Methodologies
These trends listed above employ the following popular core technologies:
- Phishing-Resistant Multi-Factor Authentication (MFA): Not all MFA is created equal. SMS-based codes are vulnerable to SIM-swapping attacks. The push is now towards phishing-resistant MFA like FIDO2 security keys and certificate-based authentication, which cannot be intercepted by man-in-the-middle attacks.
- Identity-First Security: This philosophy places identity at the very center of the security strategy, rather than treating it as just one component. It means designing security controls around the user's identity context (who they are, their device, location, etc.) before granting access to any resource.
- Decentralized Identity (Self-Sovereign Identity - SSI): A revolutionary concept where users own and control their identity data without relying on a central authority (like a government or social media platform).
- How it works: Uses blockchain or similar distributed ledgers to create verifiable credentials (VCs) and decentralized identifiers (DIDs). User could prove his age to a service without revealing his birthdate or even name.
- Machine Identity Management: With the explosion of APIs, microservices, IoT devices, and RPA bots, non-human identities now vastly outnumber human ones.
- Focus: Managing and securing credentials, certificates, and API keys for machines with the same rigor as human identities. This is critical for preventing automated attacks.
Advanced Capabilities & User Experience
In parallel with the advance technology and methodology chnages, there are also some significant enhancements:
- Continuous Adaptive Risk and Trust Assessment (CARTA): This extends beyond a one-time login check. CARTA systems continuously monitor user behavior during a session—analyzing typing patterns, mouse movements, access patterns, and location—to calculate a dynamic risk score. If risky behavior is detected (e.g., a user suddenly accessing data from a foreign country), it can trigger step-up authentication or terminate the session.
- Identity Governance and Administration (IGA) 2.0: Modern IGA platforms are becoming more intelligent and automated..
- Features: AI-driven access certification, role mining, and just-in-time (JIT) access, which grants elevated privileges only when needed for a specific task and automatically revokes them afterward.
- Customer Identity and Access Management (CIAM): This specialized area is booming as businesses focus on digital experience.
- Trends: Seamless and secure login experiences (e.g., social login, progressive profiling), privacy and consent management (for GDPR/CCPA compliance), and leveraging identity data for personalized customer analytics

The Role of AI and Machine Learning
AI is becoming the brain behind modern IAM systems, powering several key functions:
- Anomaly Detection: Identifying unusual login times, locations, or access patterns that signal a potential compromised account or insider threat.
- Automated Threat Response: Automatically blocking or challenging suspicious login attempts based on AI-driven risk scores.
- Access Policy Optimization: Analyzing vast amounts of access data to recommend and refine least-privilege policies.

Rosy Outlook Of The IAM and Broader Ecosystem Trends
- Convergence of IAM and Security: IAM is no longer an isolated IT function. It's deeply integrated with Security Orchestration, Automation, and Response (SOAR) and Security Information and Event Management (SIEM) systems to provide a unified security posture.
- Identity for the Extended Enterprise: Managing secure access for a complex web of employees, contractors, partners, and customers, all from a single, cohesive platform.
In essence, the rosy future of IAM is adaptive, context-aware, and user-centric. It's shifting from a static, one-time gatekeeper to a dynamic, intelligent system that balances robust security with a seamless user experience.